KIO4_Terminal.Run
commandLine ping -c 1 google.com
or
ping -c 1 https://www.google.com
I meant to say that currently we get result after executing all the command.
Can we get result asynchronously? Like in shell or cmd.
not possible with this extension, this is a workaround:
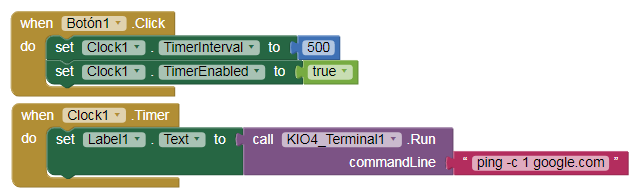
I am finding on my Android 10 & 11 devices that there is nothing reported back with
ls /system/bin
System command files are there though. If you type:
which ls
you should get back
/system/bin/ls
Thanks Google 
Hello i Tried it but nothing happend...must i be rooted to use it ?
yes, as already mentioned
Taifun
Hi,
Is there an option to call this two commands in app inventor when button is clicked?
1) adb shell settings put global private_dns_mode off
2) adb shell settings put global private_dns_specifier some.dnsWith this extension you cannot call ADB when you press a button in the application.
It is possible but not easy to set up ADB like that. Instead, I suggest you set up Termux-ADB and use an ActivityStarter to run the command in Termux. You may need to root your device or unlock it's bootloader.
Actually I was wrong, I don't think it will work with ActivityStarter, but it should be fairly simple to make an extension to run things in termux. See this comment for info on how to do it.
Yes, that is where I have been looking. Most things make sense for Activity Starter, but not sure about this one:
- Third-party program must declare com.termux.permission.RUN_COMMAND permission and it should be granted by user.
Screen1.requestPermission maybe?
How can I install curl 7.58.0 on my phone? Thanks.
You will probably need a rooted device.
Alternatively, if you have the patience, you could use Termux.....
Hello everyone!!! ![]()
![]()
![]()
I wanted to know (roughly) what is possible and what is not possible through this extension and commands.
I saw that many have problems with the issue of asynchronicity of functions and calls, but that can be fixed using the extension Async Procedures and Background Tasks also with View Pager and Dynamic Components
Added to the Web Component to make calls to APIs such as FireBase and Supabase; you will have tons of options that can only be limited by your knowledge and imagination.
<Scripts>, even an entire code or procedures.For this reason, I need to know what the scope of this extension is and if it depends on whether the phone is rooted or connected by USB, Bluetooth, Wi-Fi, etc.
Because if it's "up to your imagination"... this is going to get crazy!!!.
I'm working on an App where security is crucial, to the point that the USB issue is driving me crazy.
With some friends we were doing some security analysis (penetration, injection, sniffing, memory scan, etc.)
And for reading the forum in search of ideas, techniques, etc. I came across this post, which automatically caught my attention.
Well, as Tony Stark said:


So I would like to know (based on your experience and knowledge), how much can be done with this extension.
Functionality will depend on several factors:
Finally:
everything is hackable, with the right tools
Start reading this thread from the beginning to the end
Yes
Taifun
So far the only "setback" with the extension is that it doesn't have the "Got Output" event that the component in Kodular does (which would save a lot of time).
But it can be supplemented through other techniques and strategies.
My friends and I are already evaluating some of them, which in themselves work for the purposes (even more) but there lies the problem of the ethical use of knowledge.
One of my friends is " BackTrack Lover " [Kali, NetHunter] and he knows more about security issues and all that stuffs.
And as for security about "reverse engineering", we also have an approach where; They only find the name of some variables (unreadable), calls to the api functions on the server (with unrecognizable parameters), the creation of components dynamically (from unknown returns from the api), There are no credentials, passwords, users or any information stored.
This is also why shell commands are an improvement in the code, since (even in their most limited use), they allow you to do things that cannot be done through appinventor.
That's without mentioning whether the user is "root" (which, simply knowing it), gives you another picture, without even making use of the super user.
Regarding the sniffing of the packages that are sent and received with the calls and callbacks to and from the API. We also take measures so that they literally do not find anything useful, even if they have the public ApiKey.
This has already been tested and gave more than satisfactory results.
My friend is caring more about the "capturing information from memory" problem right now.
The idea of this App that I am creating is to maximize the options of these platforms that are often underestimated for their "lack of control" in terms of the code and their limited options.
As well as other things in terms of information, data, user monitoring, hyper sensitive information.
And obviously the importance of free and open development platforms, and the need for them to receive the support they deserve, so that access to technology, knowledge and tools is universal and is only limited by the knowledge one has.